Welcome to our comprehensive examination of the permissions settings within the newly evolved Camms.Risk. This analysis delves into the disparities between legacy and the permissions of the evolved version of Camms.Risk, providing an understanding of standard permissions and their alignment with staff-assigned roles.
Curious about streamlining your risk management workflows and enhancing user experience? Our blog post serves as your guide to unraveling intricacies and elevating your user experience. Keep reading to discover practical insights, and unlock the power of refined settings to take your risk management practices to the next level.
Legacy vs. Risk Evolved Permissions
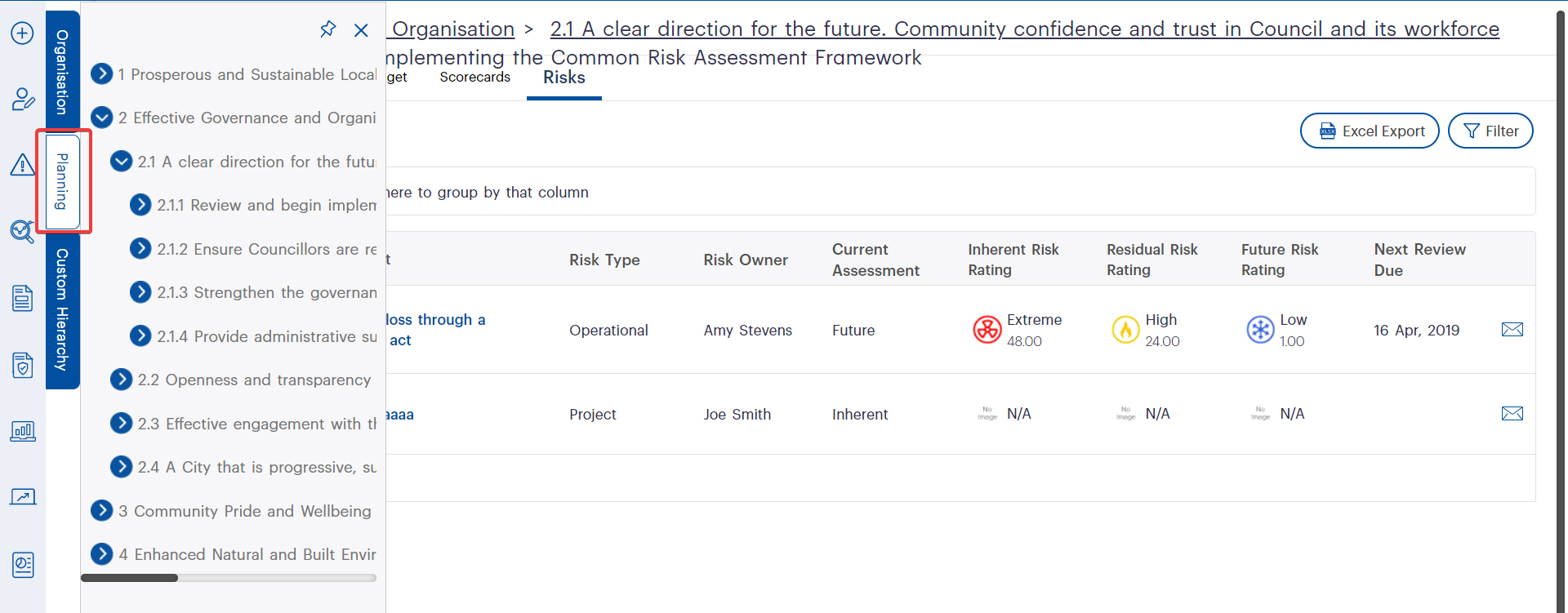
Let’s dive into a comparison of legacy and enhanced permissions in the new Camms.Risk. In the traditional setup, hierarchy configuration flexibility had its limitations. Operational users were confined to either viewing and editing all entries in a register or being restricted to editing only their assigned tasks. Enter the newly evolved Camms.Risk-a game-changer. It brings a dynamic approach that simplifies complex permission structures, offering users a more intuitive and efficient experience.
Here’s Why Camms is a Suitable Solution
When selecting permission structures, the evolved version of Camms.Risk stands out as the preferred solution. Its dynamic and flexible approach starkly contrasts with legacy systems. Unlike its predecessors, Camms.Risk Evolved simplifies hierarchy configurations, offering users a more intuitive system to navigate and configure their roles. The solution not only enhances hierarchy configurations but also streamlines the entire process, ensuring a user-friendly experience for configuring roles and navigating the system. When it comes to permissions, the choice is clear: the newly evolved Camms.Risk is the way forward.
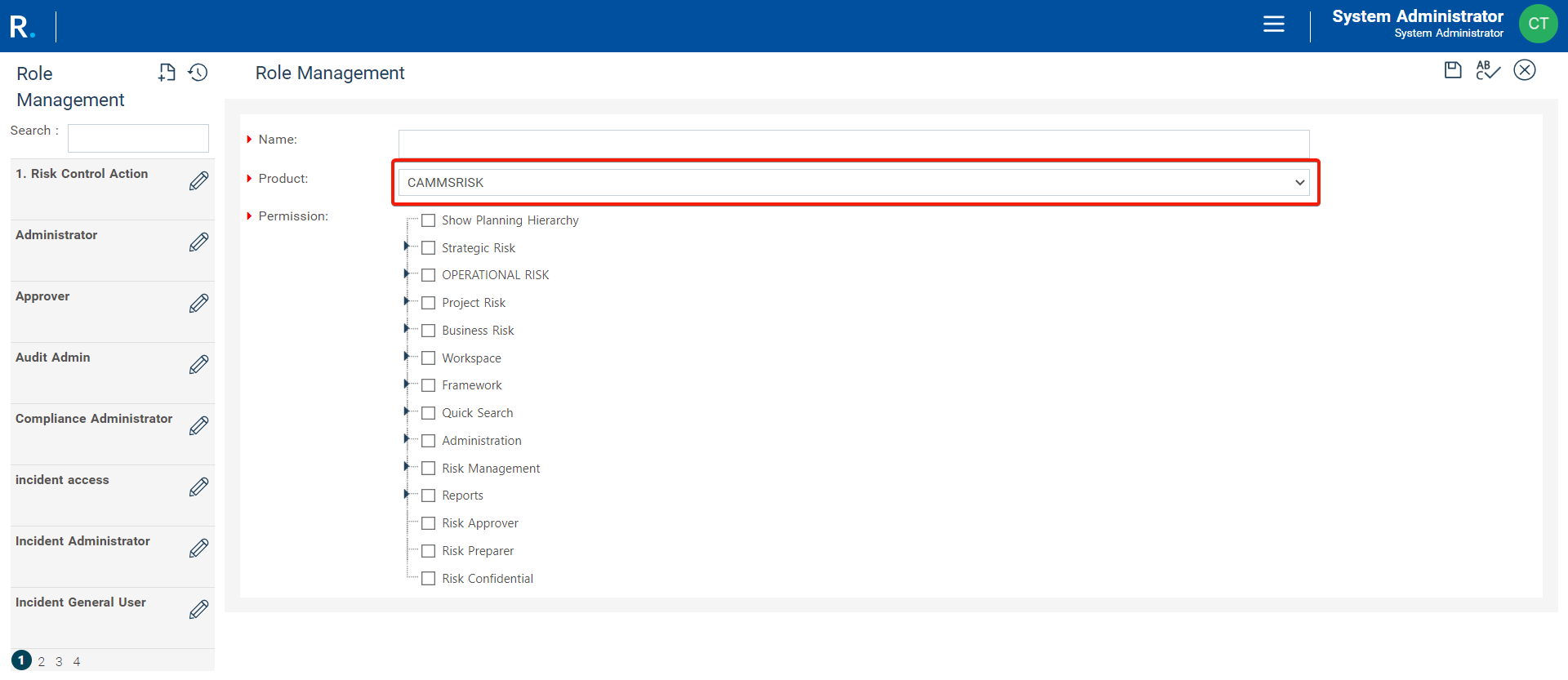
Understanding Standard Permissions
Standard permissions are the backbone the newly evolved Camms.Risk, acting as inherited roles based on user responsibilities. For instance, a risk responsible officer inherits permissions related to their specific duties. The flexibility lies in configuring these roles within the risk settings under the framework.
Optimal Setup for Permissions
Now, let’s delve into the recommended three-tier setup for users: Operational Users, Unit Managers, and Super Users.
Operational Users
Operational users typically require the most streamlined permissions. For optimal setup:
- Grant view and edit rights only to what they’ve been assigned.
- Leverage standard permissions for register visibility.
- Customize access to dashboards, reports, and workspace.
Unit Managers
Unit managers need broader visibility. Optimal settings include:
- View all linked nodes with child nodes for register visibility.
- Maintain view-only access to records with flexible editing options.
- Configure access to reports, dashboards, and workspace.
Super Users
Super users, often data administrators, necessitate comprehensive permissions. The setup involves:
- Full edit rights across all registers.
- Administer data without accessing settings.
- Enable risk approval and review prior to approval.
- Grant visibility over the entire risk workflow.
Configuring Standard Permissions
The flexibility of the new Camms.Risk shines through in standard permissions. Configure them based on responsible officers, secondary responsible officers, and action owners. Tailor access to specific tabs within the risk workflow to strike the right balance between visibility and control.
Conclusion
Permissions play a pivotal role in optimising user experience and data integrity within the new Camms.Risk. By understanding the nuances between legacy and the newly evolved permissions, configuring standard roles, and adopting the recommended three-tier setup, users can harness the full potential of this risk management tool.
For more information on the new Camms.Risk Permissions and Staff Management, click here.
For more information on Camms.Risk Incident Permissions and Staff Management, click here.
For more information on Camms.Risk Compliance Permissions and Staff Management, click here.
For further assistance or personalised guidance in configuring your permissions, feel free to schedule a virtual consulting session through Camms College.
To get an in-depth view of permission settings and master the intricacies of the evolved version of Camms.Risk, don’t forget to watch our on-demand webinar, ‘Mastering Camms.Risk Evolved: Permission Settings.’