The world has changed drastically over the past two years due to the global pandemic. What we initially thought would be a temporary spate of lockdowns lasting just a few months has gone on for much longer, and this has had a lasting impact on how we learn, how we do business, and how we interact with each other in the ‘new different’.
The reality is that the world has been collectively pushed to embrace digital – be it remote working, purchasing daily needs online or having social interactions virtually. While it is great that organisations have adopted digital and moved operations and services online at an unprecedented rate, it also means that businesses have been introduced to new challenges, vulnerabilities, and potential threats.
What Is the Impact for Businesses?
The escalation of digitisation in enterprises also means an escalation of possible cybersecurity risks. These risks can affect all types of businesses and industries, and are generally caused by misconfigurations in IT systems, lack of security awareness, and deliberate malicious attacks from hackers.
For example, with remote working taking the forefront in the past year, organisations have been required to deal with a new set of vulnerabilities stemming from the fact that employees are using personal devices and networks that don’t have the same level of security as corporate-owned devices and networks do.
We know that unmanaged cyber risks can lead to severe cyber-attacks and breaches in security, which can result in financial loss, operational breakdowns, and drastic drops in productivity and efficiency. Furthermore, in an instance that sensitive data is compromised, we know that businesses can suffer a loss of reputation, trust, and credibility, not forgetting severe ramifications if injured parties take legal action.
No organisation can assume it is secure from cyber risk because the threats keep evolving and increasing. Therefore, it is important to have an understanding of what these threats are and how they can attack your organisation’s vulnerabilities.
What Are the Key Types of Cybersecurity Threats?
Below are some of the key cybersecurity threats that frequently affect enterprises.
Hacking – refers to all attempts to access or compromise electronic systems, including a company’s website, applications, customer databases, financial records, etc. Hackers are motivated by a need to make a statement, gather classified information, prove the vulnerability of a security system, or for personal financial gain. Hacking is really an umbrella term for all malicious cyber-attacks that target individuals and businesses.
Ransomware – is malicious software planted by cybercriminals in a company’s system to block access to important information. The affected data is encrypted so that users cannot access files, applications, and databases, leading to a breakdown in operations. The attackers then demand a ransom to restore access, often requesting payment in cryptocurrency. Software vulnerabilities, remote desktop protocol, and phishing emails are some of the common attack vectors for ransomware.
Malware – is malicious software that is installed on a device or enterprise network and used to access data or sensitive information without the individual’s or company’s knowledge. This software can encrypt information, delete data, steal sensitive information, take control of core computer functions, and even spy on the victim’s activity without their knowledge.
Malicious code – a code or link that contains harmful files or programs that can damage computer functions or destroy files and data. They come in the form of viruses, worms, Trojan horses, and malicious data files. The most common attack vectors are downloads or attached files.
Social engineering or phishing – refers to an attack in which attackers use social interaction to collect information that belongs to an individual or organisation. The criminal will pose as a new employee, a researcher, or a credible company to gain personal information. Attackers may use official letterheads in emails, sophisticated websites, or phone calls to make the inquiry seem official and credible.
Foundations of Cyber Risk Management Tools
To effectively identify your organisation’s cybersecurity threats, using a cybersecurity risk assessment tool is essential. Today, this is increasingly becoming the responsibility of governance, risk, and compliance professionals to effectively identify, manage and communicate the cyber risks of the organisation using cyber risk management tools. But what are the critical capabilities that these risk management tools must offer in order to automate your cybersecurity risk assessment?
- Manage cyber risk in a systemised, transparent way from the initial incident through to detailed investigation and closure.
- Offer real-time visibility of risks and controls.
- Manage complex structures of compliance requirements for standards such as ISO 27001, NIST, HIPAA, PCI DSS, SOC 2, and GDPR Cyber Incident Management integrating your operational IT and security systems to provide a holistic view of cyber risk.
- Cyber Incident Management links incidents to risks and enables the analysis of potential controls that are failing.
- Cyber Audit Management to prepare for internal and statutory reporting obligations.
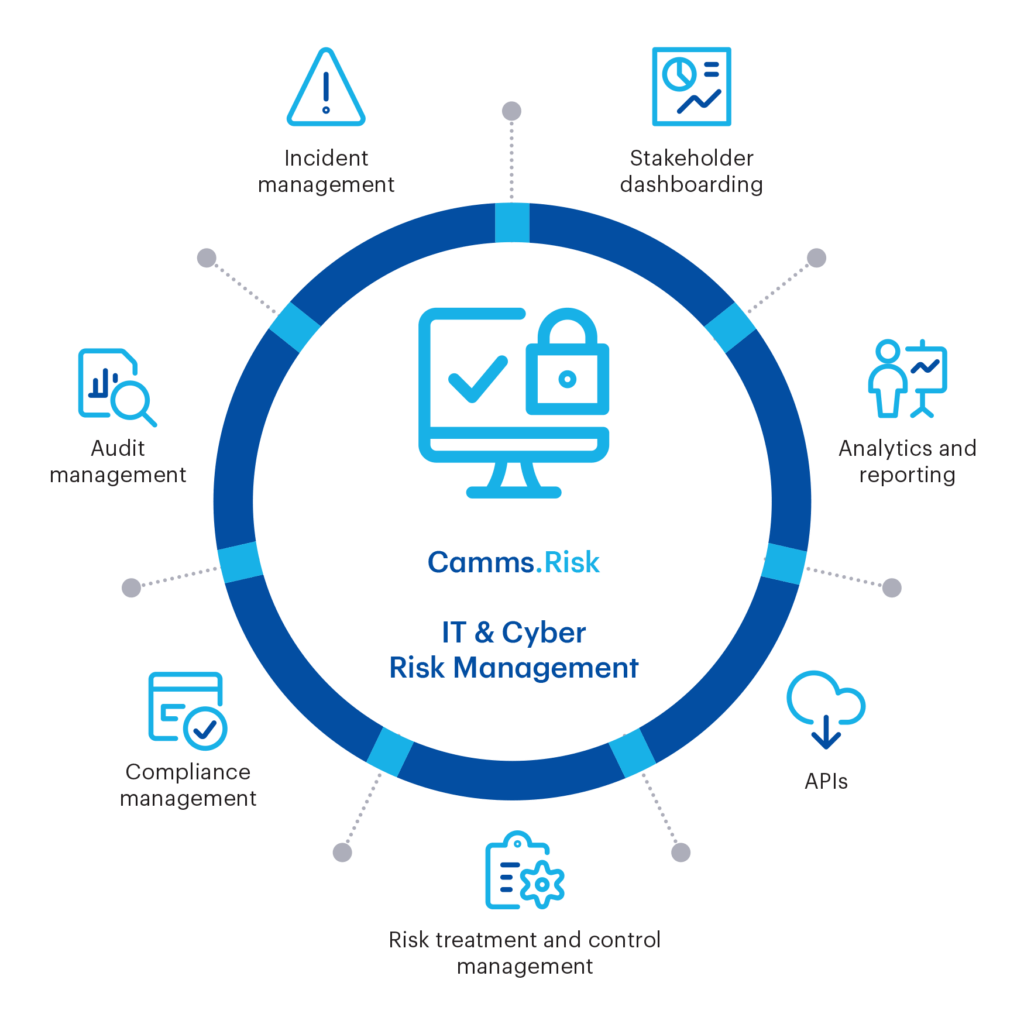
Camms.Risk Cyber Risk Management
Camms.Risk is an intelligent and flexible risk management software that provides critical insights and decision-making in a fast-paced, ever-changing business environment. It’s the best tool to manage risk, including cyber and IT risks.
In conclusion…
As the world becomes more digitised, and technology takes on a more significant role in the operations of all types of businesses, we have to accept the fact that there will always be new threats in cybersecurity to deal with. No organisation is immune, no matter how secure they believe its systems to be. The best way to prepare for an impending crisis is to have a comprehensive and efficient cybersecurity risk management plan in place, and to get the buy-in of the entire organisation, starting from the top, at the board level.
If you need advice regarding the best cybersecurity risk management approach for your organisation, get in touch with our panel of experts. Camms.College customers can schedule a meeting with a Camms Consultant by clicking here. It’s really that easy.















